
Single Sign-On with Okta (SAML)
Learn how to configure Okta as a SAML-based identity provider. Create a SAML Connection for a New App Leave this browser tab open as you proceed
Complete Cybersecurity architecture, implementation, and deployment of information security controls for Startups, or mature enterprise organizations.
We adhere to the holistic Zero Trust Security model in combination with NIST info security frameworks, across existing processes and controls, as well as fill out the gaps and eliminate your organization’s blind spots!
We do not rely on checklists, we look at your total exposure to identify threats and mitigate possible attack vectors. We offer a complete turn key solution that can cover your overall Cybersecurity posture, your Cloud infrastructure and compliance program – all delivered a whole solution.
At Prodigy 13 we utilize next-gen security solutions, powered by AI assisted capabilities, with a combination of enforcing the strongest standards for security benchmarks and compliance frameworks.
We guarantee that your organization will see immediate improvements in security posture and defense capabilities, and satisfy the information security triad at 100% (Confidentiality, Integrity, and Availability).

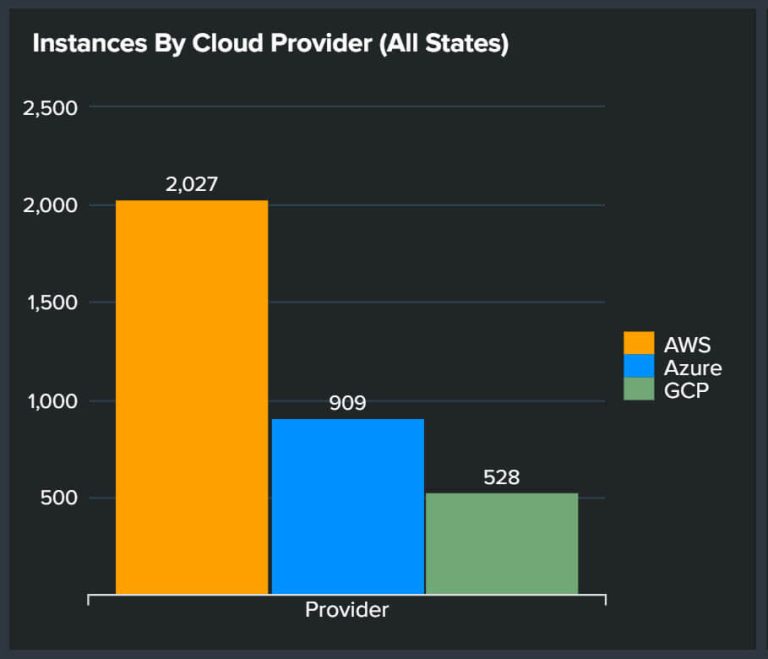
Our managed or assisted Cybersecurity service, covers anything from public Cloud providers, on site infrastructure to application security (SDLC), and compliance.
Zero Trust based Cloud, On-site or Hybrid Architecture, Implementation, Management, Monitoring, Compliance & Audit assistance, On-Demand Consultation, Training.
Specialty service in securing Remote workforce, and distributed teams
Cybersecurity is no longer considered just a “business expense”, but an investment in the future of your organization, which can have a crucial impact on your success. According to this Gartner’s prediction:
By 2025, 60% of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements

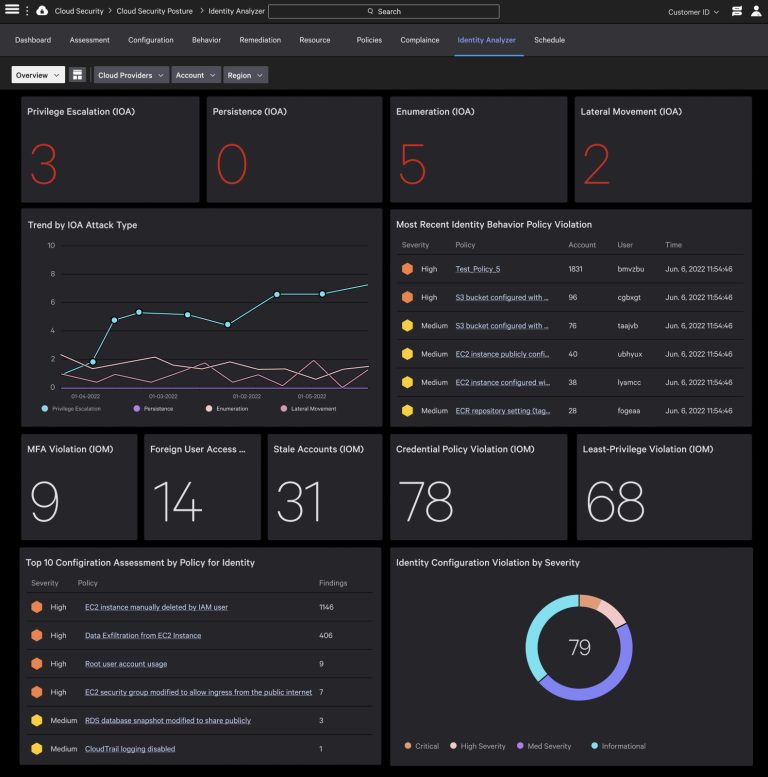
Holistic approach based on the Zero Trust Security model, ensuring 100% coverage with Zero (0) blind spots
Affordable fees, costing fraction of the cost for a typical Senior Security Engineer or other MSSP (Managed Security Service Providers) with strict deliverables and SLAs.
Services, and team members adhering to the highest security frameworks, benchmarks and standards (NIST 800-53, FedRamp, CIS, MITRE ATT&CK)










Build and run applications knowing they are protected. Take an adversary-focused approach that provides automated discovery, continuous runtime protection, EDR for cloud workloads and containers, and managed threat hunting, enabling you to securely deploy applications in the cloud with greater speed and efficiency.
Build and run applications knowing they are protected. Take an adversary-focused approach that provides automated discovery, continuous runtime protection, EDR for cloud workloads and containers, and managed threat hunting, enabling you to securely deploy applications in the cloud with greater speed and efficiency.
Build and run applications knowing they are protected. Take an adversary-focused approach that provides automated discovery, continuous runtime protection, EDR for cloud workloads and containers, and managed threat hunting, enabling you to securely deploy applications in the cloud with greater speed and efficiency.
Build and run applications knowing they are protected. Take an adversary-focused approach that provides automated discovery, continuous runtime protection, EDR for cloud workloads and containers, and managed threat hunting, enabling you to securely deploy applications in the cloud with greater speed and efficiency.

Learn how to configure Okta as a SAML-based identity provider. Create a SAML Connection for a New App Leave this browser tab open as you proceed

SAML explained in plain English: https://www.onelogin.com/learn/saml SAML is an acronym used to describe the Security Assertion Markup Language (SAML). Its primary role in online security is

Resource: https://www.threathunting.net/files/hunt-evil-practical-guide-threat-hunting.pdf To begin, let’s clarify what threat hunting is: Threat hunting is the human-driven, proactive and iterative search through networks, endpoints, or datasets in








